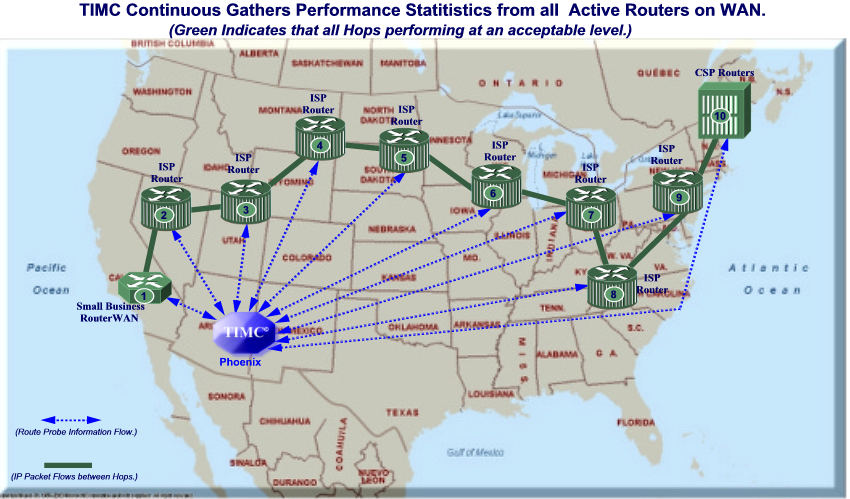
|
Technology
Infrastructure Management Console© (TIMC)
Server
|
|
The TIMC is a
new,
revolutionary
technology
infrastructure
management
architecture
that provides
proactive, 24/7
end-to-end
management
services for
small businesses
that have
migrated (or
that are in the
process of
migrating) their
business-critical
applications and
databases to a
Cloud Service
Provider (CSP).
The TIMC:
-
Operates in a proactive management mode, and
in many instances will detect, isolate, and correct
infrastructure-related problems before they disrupt services to end
users.
-
Includes a Technology Infrastructure
Management Service (TIMS) database that contains a detail inventory
of all components included in the customer's technology
infrastructure.
-
Includes Technology Infrastructure
Management Information
that performs speed tests, route probes, and application probes at pre-defined scheduled
intervals (up to four times per hour).
-
Receives realtime availability status and
informational feeds from a variety of sources.
-
Includes a web application that can display
realtime performance and availability statistics on any Internet browser.
-
Provides a variety of monthly, quarterly,
annual, and on-demand performance and problem reports.
All performance and problem statistics are
archived on the TIMC's archival database, and are available to customers
upon request.
|
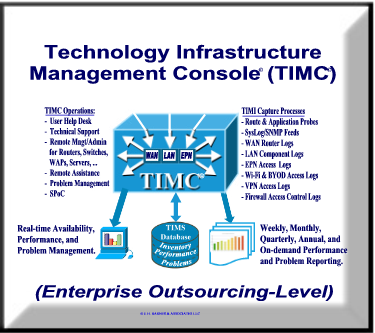 |
|
Top 10 Benefits the
Technology Infrastructure Management Console (TIMC)
|
- It provides end user
help desk
support for all problems and inquiries related to your
technology infrastructure. (The performance and
problem information contained on the TIMS database can be used
by the help desk technician to determine if the problem being
reported is a new or an existing problem. If it is a new
problem, the technician will create a trouble ticket that
includes all of the pertinent information regarding the
problem.)
|
- It is your
single-point-of-contact with
network hardware
vendors, Internet Service Providers (ISPs), and End-Point
Networking (EPN) device vendors. (Contact
information for ISPs, CSPs, web hosting companies, and all
hardware vendors are included in the TIMS inventory database.
The fact that our TIMC specialist will know who to call and the
exact nature of the problem will dramatically reduce the problem
resolution phase.)
|
- It
greatly-simplifies your hardware
requirements, and
thus dramatically-reduces your hardware cost
by streamlining and optimizing the hardware acquisition
and hardware utilization processes. (The network
and hardware performance statistics contained in the TIMS
database can be analyzed to determine if LAN hardware and/or
WAN link speeds needs to be upgraded. If so, a decision can be
made whether to upgrade horizontally – by simply adding
more of the same hardware or links, or vertically – by
replacing the specified component with a larger, more powerful
component of the same type or link with a faster link.)
|
- It ensures that your
cloud computing, web, social network,
and legacy applications can be
seamlessly and instantaneously accessed by your
LAN-attached and/or WAN-attached end-point networking devices.
(The TIMC's VPN connections are used to verify
end-to-end connectivity of cloud computing servers, Internet
hosting servers, social networks, and legacy application servers at predefined intervals, e.g., every 5
minutes.)
|
- It
provides a
formable access security barrier
that ensures employee-owned Bring-Your-Own-Devices (BYODs)
are prohibited from accessing mission-critical business
applications and databases located on cloud, web and legacy servers.
(The TIMS inventory database will include all company-own
Wi-Fi laptops, tablets, and smartphones, and will only allow these
"registered" devices to access business-critical applications.)
|
- It
mitigates
network intrusions by proactively identifying and blocking
known hacker attacks such as varies Denial-of-Service (DoS)
attacks including Win Nuke, flooding attacks, and smurfing
attacks. (Log records from routers, managed
switches, and WAPs are continuously analyzed to determine if
intrusions attempts or other hacker attacks are in progress. If so,
all information
regarding the attack is captured and a intrusion-attack trouble
ticket is created. An attempt will be made to identify the IP
address and port number of the intruder, and if this is
successful, this information along with the data captured during
the intrusion attempt will be forwarded to the proper
authorities.)
|
- It
includes an online
Technology Infrastructure Management
Services (TIMS) database that contains all of
your company's LAN hardware and company-owned end-point
networking devices. (This database includes
all pertinent information regarding the LAN and EPN devices
owned by your company, including location, type, manufacturer,
model number, serial number, Static IP address, MAC address, and
date placed in services. This database is updated on an on-going
basis and upon request, copies in Excel spreadsheet format can be sent to your
accounting and asset management departments.)
|
- It
proactively monitors your Internet Service Providers (ISPs),
Cloud Service Providers (CSPs), and selective TIMC web URLs to
ensure that they are delivering the advertised network speeds
and quality of service. (The TIMC performs speed tests
and sends specially-configured route probe packets on a frequent, scheduled basis to determine the
routing paths, download speeds, upload speeds, jitter, and latency of the links between the
customer's WAN router and selected component within the
Internet. These statistics are stored in the TIMS
database and can be used for both analyzing problems and
creating network
performance reports. They are also archived on a SQL database so
that the performance of these components can be tracked and/or
compared on a monthly, quarterly, or annual basis)
|
- It maintains image copies of the configuration of
all routers, switches and WAPs, and this ensures that if one of
these components fail; new component can be acquired, loaded
with the backup configuration, and placed online. (This
backup copy of the configuration can also be used if one of the
devices has to be "hard reset" to the original factory
configuration.)
|
- It monitors the firmware release levels in all LAN
components, and when a new firmware revision is released, it is
downloaded and installed in the designated LAN component.
(New firmware is periodically released by
manufacturers to fix bugs and to add new functionality, and
tracking the firmware release of each LAN component ensures that
it is performing at maximum efficiency.)
|
- It
supports all major end-point devices such as PCs, MACs, tablets, smartphones, and other
devices that support the IPv4/IPv6 protocol standards.
(All end-point networking devices have identifying
characteristics such as: 1.) static or DHCP assigned IP
addresses, 2.) Media Access Control (MAC) addresses, and 3.) EPN
device name. This information is logged into the TIMS database
each time an EPN logs into the network. Other pertinent
information such as the destination URL, length of session, and
amount of data sent/received, is also captured.)
|
- It
includes two different client Virtual Private Network (VPN)
implementations which will allow your traveling and
telecommuting employees to securely access business-critical
applications and databases residing on the LAN, WAN, and/or
cloud computing servers. (The TIMS VPN
implementations support up to fifty-five encrypted tunnels that
offers the same level of access security to your travelling and
telecommuting employees as is provided to your employees
attached to the LAN via wired connections.).
|
- It provides proactive monitoring and problem
management services to your branch offices and remote locations
ensuring that all components of your technology infrastructure
are performing at the highest level possible.
(Your new technology Infrastructure includes a
gateway-to-gateway VPN implementation that is ideally suited for
including the routers, switches, and WAPs located at branch
offices and remote locations in the LAN.)
|
- It archives all performance statistics, problem
logs, and SysLog records on a secure SQL Server 2012 database
for up to one year. (This information can be used to
create annual performance and problem reports that can be used
for traffic growth projections and budgeting forecasts.)
|
- It
provides
monthly, quarterly, annual, and
on-demand performance and problem reports that
can be used to identify problems or potential problems before
they occur. (Summary versions of these
reports can be viewed online or can be sent designated members
of your staff electronically.)
|
The above is only ten of the many features of the TIMC. If you
would like to learn more about any aspect of the TIMC, please call
623-979-1827 or 602-478-4778.
Click Here to get
printable-version of
benefits listed
above. |
|
|
|